Configuring NG Firewall for AWS using routed subnets: Difference between revisions
Bcarmichael (talk | contribs) m (Bcarmichael moved page AWS Install to Configuring NG Firewall for AWS using routed subnets: title needs to be more descriptive to make way for other topics related to AWS deployment) |
Bcarmichael (talk | contribs) |
||
| (42 intermediate revisions by the same user not shown) | |||
| Line 1: | Line 1: | ||
= | == Overview == | ||
[[File:Aws_schemas_advanced.png|thumb|right|upright=1.4|alt=Untangle NG Firewall in relation to AWS instances and VPN tunnels.|Untangle NG Firewall in relation to AWS instances and VPN tunnels.]]Untangle NG Firewall deployment in AWS can secure Internet access for other AWS instances. This scenario is useful if you have for example [https://aws.amazon.com/workspaces Amazon Workspaces] and you need to apply Intrusion Prevention, Content Filtering, Bandwidth Control, and other next generation firewall capabilities to those instances. This type of deployment requires advanced Virtual Private Cloud (VPC) configuration to establish an internal subnet for AWS instances that routes through NG Firewall. | |||
== Before you begin == | |||
*Follow the steps outlined in [https://wiki.untangle.com/index.php/Deploying_NG_Firewall_in_AWS Deploying NG Firewall in AWS]. | |||
*Review [https://docs.aws.amazon.com/AmazonVPC/latest/UserGuide/VPC_Subnets.html VPCs and Subnets] in the AWS documentation. | |||
== Step 1. Configure a Security Group == | |||
AWS instances and network interfaces inherit traffic rules defined by [https://docs.aws.amazon.com/vpc/latest/userguide/VPC_SecurityGroups.html security groups]. The security group assigned to your NG Firewall instance and instances on the private network behind NG Firewall should have an open policy to avoid conflicts. Confirm that the security group designated for your instances has rules to permit all incoming and outgoing traffic. | |||
#In the [https://aws.amazon.com/console AWS Management Console] go to your VPC configuration from the '''Services''' menu. | |||
#Click '''Security Groups'''. | |||
#Select the default security group or a custom security group you designate for instances belonging to your internal subnet. | |||
#In the Inbound Rules tab, click '''Edit'''.[[File:Aws-securitygroups-inbound.png|none|thumb|upright=1.2|Security group with permissive inbound rule]] | |||
#Add or confirm a rule allowing all traffic for all protocols where the source is 0.0.0.0/0. | |||
#Confirm this same policy in the Outbound Rules tab. | |||
== Step 2. Configure a Network ACL == | |||
[[File:Aws-networkacls-inbound.png|thumb|upright=1.5|Network ACL with permissive inbound rule]]Each subnet inherits the policies of [https://docs.aws.amazon.com/vpc/latest/userguide/vpc-network-acls.html network ACLs]. Confirm that the network ACL designated for your internal subnet contain rules to permit all incoming and outgoing traffic. | |||
#In the [https://aws.amazon.com/console AWS Management Console] go to your VPC configuration from the '''Services''' menu. | |||
#Click '''Network ACLs'''. | |||
#Select the default network ACL or a custom network ACL if designated for your internal subnet. | |||
#In the Inbound Rules tab, click '''Edit'''. | |||
#Add or confirm a rule allowing all traffic for all protocols where the source is 0.0.0.0/0. | |||
#Confirm this same policy in the '''Outbound Rules''' tab. | |||
== | == Step 3. Create an internal subnet == | ||
[[File:Aws-subnet-wiz.png|thumb|upright=1.2|AWS subnet configuration wizard]]To route traffic for AWS instances through NG Firewall you must designate an internal [[https://docs.aws.amazon.com/vpc/latest/userguide/working-with-vpcs.html#AddaSubnet subnet]]. You assign this subnet to network interfaces belonging to your AWS instances and NG Firewall. | |||
# | #In the [[https://aws.amazon.com/console AWS Management Console]] go to your VPC configuration from the '''Services''' menu. | ||
# | #Click '''Subnets'''. | ||
# | #Click '''Create Subnet'''. | ||
#Select the VPC containing your NG Firewall and AWS instances. | |||
#Select the same availability zone as your NG Firewall instance. | |||
#Assign an IPv4 block that is within the scope of your VPC. | |||
#Click '''Create''' to confirm the new subnet. | |||
== Step 4. Create a network interface == | |||
[https://docs.aws.amazon.com/vpc/latest/userguide/VPC_ElasticNetworkInterfaces.html Network interfaces in AWS] attach to instances and facilitate network access to the VPC. The NG Firewall and instances protected by the firewall must be assigned to the internal subnet you created in the previous step. If you created your instances and network interfaces prior to creating the internal subnet, you can create new network interfaces to associate your instances to the internal subnet. | |||
#In the [https://aws.amazon.com/console AWS Management Console] go to your EC2 configuration from the '''Services''' menu. | |||
#Click '''Network Interfaces'''. | |||
#Click '''Create Network Interface'''.[[File:Aws-create-interface.png|thumb|none|upright=1.6|AWS network interface configuration wizard]] | |||
#Select the internal subnet you created in the previous step. | |||
#Keep '''Private IP''' as ''auto assign''. | |||
#Select the permissive security group you created in the first step. | |||
#Click '''Yes, Create'''. | |||
== Step 5. Attach the network interface == | |||
[[File:Aws_attach_iface.png|thumb|right|upright=1.3|Attaching a network interface to an instance in AWS]]After you create a network interface you must attach it to an instance. | |||
#In the Network Interfaces screen select an available interface that belongs to the internal subnet. | |||
#In the '''Actions''' menu choose '''Attach'''. | |||
#Select the Instance ID of your NG Firewall | |||
#Repeat the steps for creating and attaching network interfaces for all instances that you intend to place on the internal subnet. | |||
{{Note|text=If you attach a new network interface to an instance other than NG Firewall, it is recommended to detach the previous network interface to prevent traffic from bypassing NG Firewall. To detach an interface, select the network interface and choose '''Detach''' from the '''Actions''' menu. }} | |||
== Step 6. Disable source and destination check == | |||
[[File:Aws-src-check.png|thumb|right|upright=.8|Disabling source and destination check on a network interface in AWS]]By default, the AWS VPC configuration prevents NAT routing. You must override this behavior by [https://docs.aws.amazon.com/vpc/latest/userguide/VPC_NAT_Instance.html#EIP_Disable_SrcDestCheck disabling source and destination check] for the internal network interface of NG Firewall. | |||
#In the network interfaces screen select the internal network interface attached to NG Firewall. | |||
#In the '''Actions''' menu choose '''Change Source/Dest. Check'''. | |||
#Set the value to '''Disabled'''. | |||
#Click '''Save'''. | |||
== Step 7. Create a route table == | |||
To direct traffic through your NG Firewall instance you must create a [https://docs.aws.amazon.com/vpc/latest/userguide/VPC_Route_Tables.html route table] with NG Firewall as a gateway and associate it with the internal subnet. | |||
#In the [https://aws.amazon.com/console AWS Management Console] go to your VPC configuration from the Services menu. | |||
#Click '''Route Table'''. | |||
#Click '''Create Route Table'''.[[File:Aws-create-routetable.png|thumb|none|upright=1.2|Creating a route table in AWS]] | |||
#Assign the route table a '''Name Tag''' and the '''VPC''' containing your NG Firewall and associated instances. | |||
#Click '''Yes, Create'''. | |||
== Step 8. Add a default route == | |||
[[File:Aws-default-route.png|thumb|right|upright=1.2|Adding a default route to a route table in AWS]]Before adding the default route, refer to the network interfaces screen and capture the Network Interface ID of the internal interface attached to your NG Firewall instance. | |||
# | #In the Route Table screen, select the route table you created in the previous step. | ||
# | #Select the '''Routes''' tab. | ||
#Click '''Edit'''. | |||
# | #Click '''Add another route'''. | ||
#In the '''Destination''' field, enter 0.0.0.0/0. | |||
#In the '''Target''' field, enter the Network Interface ID of the internal network interface attached to your NG Firewall instance. | |||
#Click '''Save'''. | |||
== Step 9. Associate the route table == | |||
To associate the route table to your internal subnet: | |||
#Select the new route table entry and click '''Subnet Associations''' from the configuration panel. | |||
#Click '''Edit''' and associate the route table to your internal subnet.[[File:Aws-associate-subnet.png|thumb|none|upright=1.4|Associating a subnet in AWS]] | |||
#Click '''Save'''. | |||
# | |||
# | |||
= | |||
# | |||
Latest revision as of 23:28, 14 May 2020
Overview
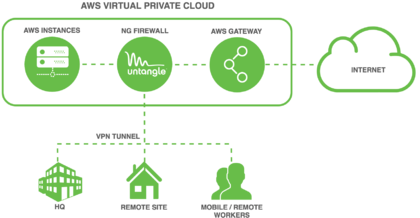
Untangle NG Firewall deployment in AWS can secure Internet access for other AWS instances. This scenario is useful if you have for example Amazon Workspaces and you need to apply Intrusion Prevention, Content Filtering, Bandwidth Control, and other next generation firewall capabilities to those instances. This type of deployment requires advanced Virtual Private Cloud (VPC) configuration to establish an internal subnet for AWS instances that routes through NG Firewall.
Before you begin
- Follow the steps outlined in Deploying NG Firewall in AWS.
- Review VPCs and Subnets in the AWS documentation.
Step 1. Configure a Security Group
AWS instances and network interfaces inherit traffic rules defined by security groups. The security group assigned to your NG Firewall instance and instances on the private network behind NG Firewall should have an open policy to avoid conflicts. Confirm that the security group designated for your instances has rules to permit all incoming and outgoing traffic.
- In the AWS Management Console go to your VPC configuration from the Services menu.
- Click Security Groups.
- Select the default security group or a custom security group you designate for instances belonging to your internal subnet.
- In the Inbound Rules tab, click Edit.
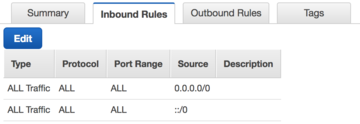
Security group with permissive inbound rule - Add or confirm a rule allowing all traffic for all protocols where the source is 0.0.0.0/0.
- Confirm this same policy in the Outbound Rules tab.
Step 2. Configure a Network ACL

Each subnet inherits the policies of network ACLs. Confirm that the network ACL designated for your internal subnet contain rules to permit all incoming and outgoing traffic.
- In the AWS Management Console go to your VPC configuration from the Services menu.
- Click Network ACLs.
- Select the default network ACL or a custom network ACL if designated for your internal subnet.
- In the Inbound Rules tab, click Edit.
- Add or confirm a rule allowing all traffic for all protocols where the source is 0.0.0.0/0.
- Confirm this same policy in the Outbound Rules tab.
Step 3. Create an internal subnet
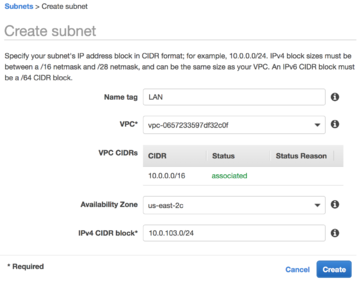
To route traffic for AWS instances through NG Firewall you must designate an internal [subnet]. You assign this subnet to network interfaces belonging to your AWS instances and NG Firewall.
- In the [AWS Management Console] go to your VPC configuration from the Services menu.
- Click Subnets.
- Click Create Subnet.
- Select the VPC containing your NG Firewall and AWS instances.
- Select the same availability zone as your NG Firewall instance.
- Assign an IPv4 block that is within the scope of your VPC.
- Click Create to confirm the new subnet.
Step 4. Create a network interface
Network interfaces in AWS attach to instances and facilitate network access to the VPC. The NG Firewall and instances protected by the firewall must be assigned to the internal subnet you created in the previous step. If you created your instances and network interfaces prior to creating the internal subnet, you can create new network interfaces to associate your instances to the internal subnet.
- In the AWS Management Console go to your EC2 configuration from the Services menu.
- Click Network Interfaces.
- Click Create Network Interface.
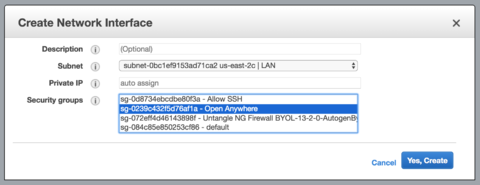
AWS network interface configuration wizard - Select the internal subnet you created in the previous step.
- Keep Private IP as auto assign.
- Select the permissive security group you created in the first step.
- Click Yes, Create.
Step 5. Attach the network interface
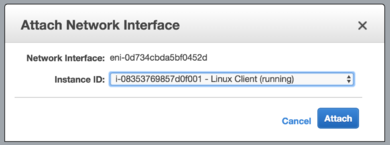
After you create a network interface you must attach it to an instance.
- In the Network Interfaces screen select an available interface that belongs to the internal subnet.
- In the Actions menu choose Attach.
- Select the Instance ID of your NG Firewall
- Repeat the steps for creating and attaching network interfaces for all instances that you intend to place on the internal subnet.
Step 6. Disable source and destination check

By default, the AWS VPC configuration prevents NAT routing. You must override this behavior by disabling source and destination check for the internal network interface of NG Firewall.
- In the network interfaces screen select the internal network interface attached to NG Firewall.
- In the Actions menu choose Change Source/Dest. Check.
- Set the value to Disabled.
- Click Save.
Step 7. Create a route table
To direct traffic through your NG Firewall instance you must create a route table with NG Firewall as a gateway and associate it with the internal subnet.
- In the AWS Management Console go to your VPC configuration from the Services menu.
- Click Route Table.
- Click Create Route Table.
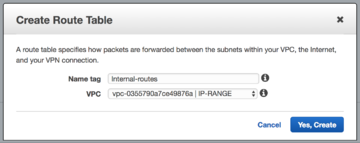
Creating a route table in AWS - Assign the route table a Name Tag and the VPC containing your NG Firewall and associated instances.
- Click Yes, Create.
Step 8. Add a default route
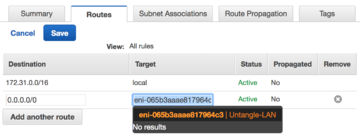
Before adding the default route, refer to the network interfaces screen and capture the Network Interface ID of the internal interface attached to your NG Firewall instance.
- In the Route Table screen, select the route table you created in the previous step.
- Select the Routes tab.
- Click Edit.
- Click Add another route.
- In the Destination field, enter 0.0.0.0/0.
- In the Target field, enter the Network Interface ID of the internal network interface attached to your NG Firewall instance.
- Click Save.
Step 9. Associate the route table
To associate the route table to your internal subnet:
