Virus Blocker: Difference between revisions
No edit summary |
|||
| Line 33: | Line 33: | ||
Virus Blocker transparently scans your HTTP, FTP and SMTP traffic to protect your network from viruses, trojans and other malware. It scans within archives such as zip, rar, tar, gzip, bzip2 (and more). | Virus Blocker transparently scans your HTTP, FTP and SMTP traffic to protect your network from viruses, trojans and other malware. It scans within archives such as zip, rar, tar, gzip, bzip2 (and more). | ||
As files are downloaded onto the network Virus Blocker scans downloads using many technologies. Firstly, it will collect metadata about the file and query the | As files are downloaded onto the network Virus Blocker scans downloads using many technologies. Firstly, it will collect metadata about the file and query the NG Firewall threat intelligence database for information about the file based on its fingerprint. Secondly, a local scan using Bitdefender's signature database will be run on the server while the cloud lookup is being performed. Thirdly, a heuristic scan is performed to look for suspicious patterns in executable files. Lastly, dynamic analysis is performed by evaluating code in a emulator and looking for malicious activity. If the download fails any of the above test it is considered malware and the download is blocked. | ||
{{:Virus Blockers Common}} | {{:Virus Blockers Common}} | ||
== Reports == | == Reports == | ||
Latest revision as of 18:42, 3 May 2022
 Virus Blocker Virus Blocker
|
|
About Virus Blocker
Virus Blocker transparently scans your HTTP, FTP and SMTP traffic to protect your network from viruses, trojans and other malware. It scans within archives such as zip, rar, tar, gzip, bzip2 (and more).
As files are downloaded onto the network Virus Blocker scans downloads using many technologies. Firstly, it will collect metadata about the file and query the NG Firewall threat intelligence database for information about the file based on its fingerprint. Secondly, a local scan using Bitdefender's signature database will be run on the server while the cloud lookup is being performed. Thirdly, a heuristic scan is performed to look for suspicious patterns in executable files. Lastly, dynamic analysis is performed by evaluating code in a emulator and looking for malicious activity. If the download fails any of the above test it is considered malware and the download is blocked.
Settings
This section reviews the different settings and configuration options available for the virus scanners.
Status
This displays the current status and some statistics.
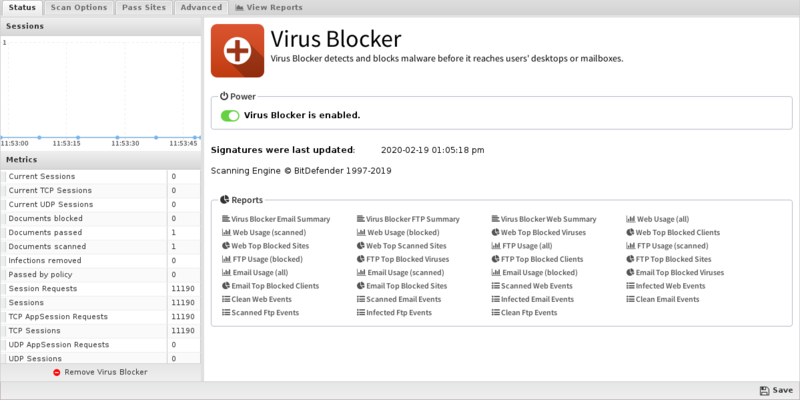
Scan Options
Scan options configure what network traffic and content to scan.
- Scan HTTP: This enables or disables HTTP scanning.
- Scan SMTP: This option enables scanning of SMTP message attachments.
- Action: The selected action will be taken on a message if a virus is found.
- Setting Action to Remove Infection will remove the infected attachment and wrap the original email for delivery to the intended recipient. If set to Pass Message, the original message will be wrapped and delivered with the attachment intact. In both cases, the subject line is prepended with "[VIRUS]". Block will block the message from being delivered.
- Scan FTP: This enables or disables scanning of FTP downloads.
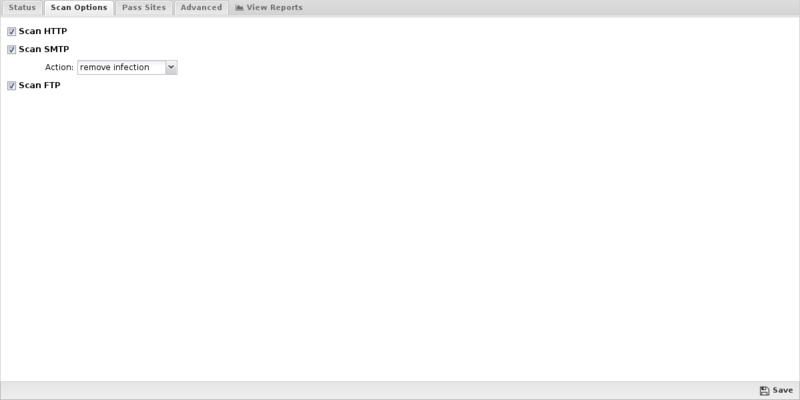
Pass Sites
This section allows you to specify sites that are not scanned. The list uses the Glob Matcher syntax.
- NOTE: Use caution when adding sites to this list!
For each protocol, the behavior is as follows:
- HTTP. Match the HTTP Host header.
- FTP. Match the server IP address or domain address (if a reverse DNS address exists).
- Email. Match the client or server IP address or domain address (if a reverse DNS address exists).
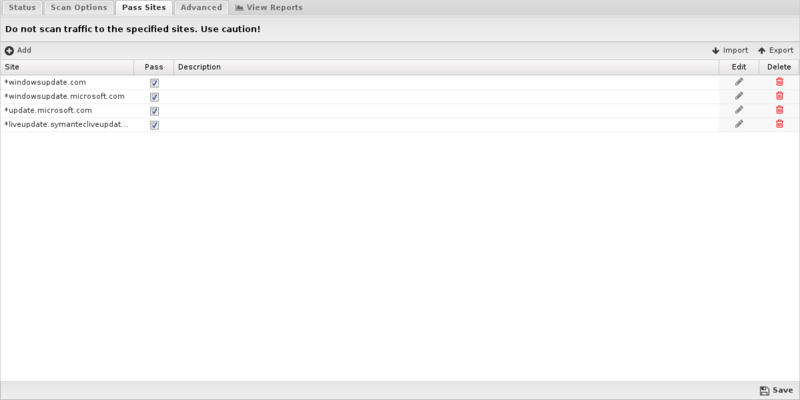
Advanced
Advanced settings can tune specific behavior of virus blocker.
The first options can enable/disable certain scanners. When a file is scanned by virus blocker, it is scanned by multiple engines, a local antivirus engine and the cloud ScoutIQ™ engine.
Using all available engines is recommended.
File extensions
File extensions configure which HTTP files will be scanned. The defaults are the recommended values. However, in some cases you may with to add or remove certain file extensions.
A understanding of security tradeoffs and pragmatism is essential before changing these settings. Unlike the other URL-based scanning of other apps like Web Filter, Virus Blocker runs in depth analysis of the file, including signatures, heuristics, and emulation. Unlike host-based antivirus, the gateway is a unique resource shared among the whole network and furthermore it has no ability to scan-on-exec as it has no knowledge of what the client plans to execute, unlike host-based antivirus. Scanning is expensive and turning on certain extensions (like .png files) can cripple the network. Analyzing reports to see how many scans are being done and if those resources are being spent on worthwhile scan resources is a good exercise. It is not uncommon to see millions of scans of some application's update.
MIME types
Similar to file extensions, but this lists the MIME types to be scanned, regardless of extension. The same logic and warnings apply here as well.
Reports
The Reports tab provides a view of all reports and events for all traffic handled by Virus Blocker.
Reports
This applications reports can be accessed via the Reports tab at the top or the Reports tab within the settings. All pre-defined reports will be listed along with any custom reports that have been created.
Reports can be searched and further defined using the time selectors and the Conditions window at the bottom of the page. The data used in the report can be obtained on the Current Data window on the right.
Pre-defined report queries: {{#section:All_Reports|'Virus Blocker'}}
The tables queried to render these reports:
Related Topics
Virus Blocker FAQs
If I use NG Firewall, do I need to install virus software on individual network computers?
We recommend an additional layer of protection on the desktop. Virus Blocker and Virus Blocker Lite scan HTTP, FTP, SMTP, and HTTPS if you are running SSL Inspector. However, there are many other ways for malware to enter the network such as through other protocols or encrypted tunnels or through physical means like a USB key.
If I have Virus Blocker and Virus Blocker Lite installed, are one or both used and in which order?
If you have both virus scanners installed, Virus Blocker is applied to a message first: if a message passes Virus Blocker, then and only then is Virus Blocker Lite applied to the message (there's no point in scanning the message twice if the first scanner has rejected it). This is not to say one scanner is inherently better than the another: note that Virus Blocker is complemented by Virus Blocker Lite and in the case of a virus-free message, the computational overhead of the virus scan includes both scanners. A message that would be rejected by both scanners incurs the computational and time cost of just Virus Blocker. To perform a valid comparison, you should run test messages through the NG Firewall with no scanners installed, Virus Blocker by itself, Virus Blocker Lite by itself and lastly both scanners installed together and compare the results.
How can I test that viruses are being blocked?
An easy way to test HTTP virus scanning is to download the eicar test from a machine behind NG Firewall. If virus scanning is not working the file will download successfully (it is harmless). If it is working a block page will be displayed.
Why do emails with larger attachments sometimes "disappear" or are not delivered?
While NG Firewall is scanning the attachments your email server is still waiting for the message, most likely triggering a timeout setting. If you're using MS Exchange, you'll want to increase the ConnectionInactivityTimeout setting.
Why does the Event Log say a file is blocked, but I can still download it?
When downloading over the web small files are blocked with a block page. Larger files are treated differently. They are fed to the client at a slower rate than they are actually downloaded so the client does not time out while the download happens. After NG Firewall scans the complete file it will either refuse to send the rest if there is a virus or immediately send the rest. This means for large files the Event Log says the file is "blocked", but checking the file size on the client will show that you do not actually have the complete file.
