RADIUS Server: Difference between revisions
Bcarmichael (talk | contribs) |
|||
| (7 intermediate revisions by one other user not shown) | |||
| Line 1: | Line 1: | ||
<span style="display:none" class="helpSource local_directory_radius_server">RADIUS_Server</span> | <span style="display:none" class="helpSource local_directory_radius_server">RADIUS_Server</span> | ||
= | = RADIUS Server = | ||
The '' | The ''RADIUS Server'' enables [https://en.wikipedia.org/wiki/IEEE_802.1X 802.1x] wireless access points to enforce authentication via WPA/WPA2 Enterprise. WPA/WPA2 Enterprise wireless networking provides an optimal level of network authorization by requiring each wireless device to authenticate with unique credentials of an authorized user rather than a shared password. Users can be authenticated against [[Local Users]] or Active Directory via the [[RADIUS Proxy]]. | ||
== Wi-Fi Authentication == | == Wi-Fi Authentication == | ||
To | To enable support for WPA/WPA2 Enterprise authentication, navigate to the '''RADIUS Server''' tab of the [[Local Directory]] and select '''Enable external access point authentication'''. In the ''RADIUS Password'' field assign a strong password. | ||
{{BiScreenshot|config|radius-server}} | |||
After you enable the NG Firewall RADIUS server you need to configure your access point to use WPA/WPA2 Enterprise. The following parameters may be necessary to configure WPA/WPA2 Enterprise for your access point. | |||
* RADIUS Server IP address - the IP address of your NG Firewall server on the same LAN segment as your wireless access point. | |||
* RADIUS port number - the NG Firewall RADIUS authentication server listens on port 1812. | |||
* RADIUS accounting port - the NG Firewall RADIUS accounting server listens on port 1813. This parameter is optional and may not be supported or configurable on some access points. RADIUS accounting is used by the access point to inform the NG Firewall server about login and logout activities of each authenticated user and their associated device address. | |||
* Shared Secret - the shared secret may also be called a password or key and is used to authorize communication between the access point and the NG Firewall RADIUS server. | |||
== Server Certificate == | == Server Certificate == | ||
When clients connect to the wireless network, they must install the root certificate of your server. See [[Certificates]]. Most devices supporting WPA/WPA2 Enterprise authentication prompt the user to install the certificate when joining the network for the first time. | When clients connect to the wireless network, they must install the root certificate of your server. See [[Certificates]]. Most devices supporting WPA/WPA2 Enterprise authentication prompt the user to install the certificate when joining the network for the first time. | ||
== Access Rules == | |||
By default there are two [[Access Rules]] to allow access to the RADIUS server from WAN or non-WAN interfaces. The access rules permit UDP protocol to ports 1812 and 1813. If your access point or domain controller does not belong to a local network then you need to enable the rule ''Allow RADIUS on WANs''. | |||
[[Image:Radius-access-rules.png|800px|center|RADIUS Server - Access Rules]] | |||
'''Note on upgrades:''' When upgrading to version 16.2 these rules are not automatically created. You must create them manually to permit access from your access point to NG Firewall. | |||
Latest revision as of 16:14, 3 May 2022
RADIUS Server
The RADIUS Server enables 802.1x wireless access points to enforce authentication via WPA/WPA2 Enterprise. WPA/WPA2 Enterprise wireless networking provides an optimal level of network authorization by requiring each wireless device to authenticate with unique credentials of an authorized user rather than a shared password. Users can be authenticated against Local Users or Active Directory via the RADIUS Proxy.
Wi-Fi Authentication
To enable support for WPA/WPA2 Enterprise authentication, navigate to the RADIUS Server tab of the Local Directory and select Enable external access point authentication. In the RADIUS Password field assign a strong password.
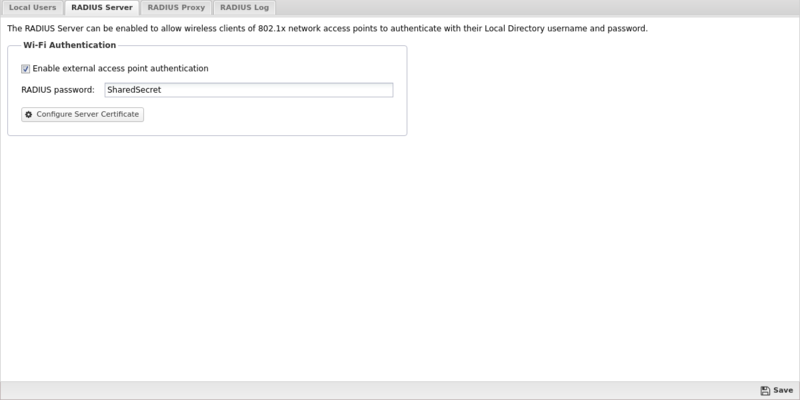
After you enable the NG Firewall RADIUS server you need to configure your access point to use WPA/WPA2 Enterprise. The following parameters may be necessary to configure WPA/WPA2 Enterprise for your access point.
- RADIUS Server IP address - the IP address of your NG Firewall server on the same LAN segment as your wireless access point.
- RADIUS port number - the NG Firewall RADIUS authentication server listens on port 1812.
- RADIUS accounting port - the NG Firewall RADIUS accounting server listens on port 1813. This parameter is optional and may not be supported or configurable on some access points. RADIUS accounting is used by the access point to inform the NG Firewall server about login and logout activities of each authenticated user and their associated device address.
- Shared Secret - the shared secret may also be called a password or key and is used to authorize communication between the access point and the NG Firewall RADIUS server.
Server Certificate
When clients connect to the wireless network, they must install the root certificate of your server. See Certificates. Most devices supporting WPA/WPA2 Enterprise authentication prompt the user to install the certificate when joining the network for the first time.
Access Rules
By default there are two Access Rules to allow access to the RADIUS server from WAN or non-WAN interfaces. The access rules permit UDP protocol to ports 1812 and 1813. If your access point or domain controller does not belong to a local network then you need to enable the rule Allow RADIUS on WANs.
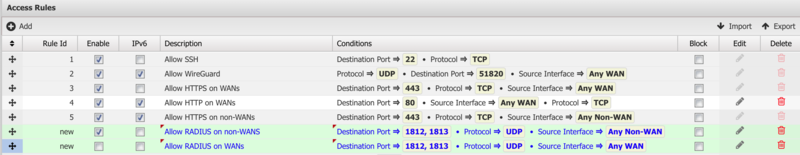
Note on upgrades: When upgrading to version 16.2 these rules are not automatically created. You must create them manually to permit access from your access point to NG Firewall.
