Policy Manager: Difference between revisions
No edit summary |
No edit summary |
||
| (5 intermediate revisions by 2 users not shown) | |||
| Line 1: | Line 1: | ||
[[Category: Applications]] | [[Category: Applications]] | ||
<span style="display:none" class="helpSource policy_manager">Policy_Manager</span> | <span style="display:none" class="helpSource policy_manager">Policy_Manager</span> | ||
<span style="display:none" class="helpSource policy_manager_status">Policy_Manager#Status</span> | |||
<span style="display:none" class="helpSource policy_manager_policies">Policy_Manager#Policies</span> | <span style="display:none" class="helpSource policy_manager_policies">Policy_Manager#Policies</span> | ||
<span style="display:none" class="helpSource policy_manager_rules">Policy_Manager#Rules</span> | <span style="display:none" class="helpSource policy_manager_rules">Policy_Manager#Rules</span> | ||
| Line 7: | Line 8: | ||
{| width='100%' | {| width='100%' | ||
|- | |- | ||
| align="center" | [[Image: | | align="center" | [[Image:PolicyManager.png|128px]] '''Policy Manager''' | ||
| align="center" | | | align="center" | | ||
{| | {| | ||
| Line 15: | Line 16: | ||
|[http://www.untangle.com/store/policy-manager-conf.html Policy Manager Description Page] | |[http://www.untangle.com/store/policy-manager-conf.html Policy Manager Description Page] | ||
|- | |- | ||
|[http:// | |[http://demo.untangle.com/admin/index.do#service/policy-manager Policy Manager Demo] | ||
|- | |- | ||
|[http://forums.untangle.com/policy-manager/ Policy Manager Forums] | |[http://forums.untangle.com/policy-manager/ Policy Manager Forums] | ||
| Line 30: | Line 31: | ||
== About Policy Manager == | == About Policy Manager == | ||
Policy Manager is one of | Policy Manager is one of NG Firewall's most powerful features. It works by allowing you to create multiple policies, which are different sets of applications configured differently for different use cases. Often you will configure all of NG Firewall apps to service the whole network, however often it is necessary to handle traffic for some users or network devices differently. For example, you may want Web Filter to be different for students vs teacher and you may want no Web Filtering at all for your servers. You may wish to run Captive Portal but only on the WiFi network or for unidentified devices. You may wish block certain applications with Application Control, but only at certain times of days. | ||
In these cases, Policy Manager can simplify configuration a great deal by allowing for multiple sets of applications to be configured differently. | |||
Policy Manager allows creation of new policies beyond the "Default Policy". To address the above examples, the administrator can create a "Student Policy", "Teacher Policy", "After hours Policy", and "Wireless Network Policy" etc. Each policy can run a different set of applications configured differently. The Policy Manager Rules can determine which policy handles which network sessions. | |||
* Set up multiple policies for different users, hosts, networks, interfaces, times of day, days of week, etc. | |||
* Choose what applications are running in each policies. | |||
* Configure multiple applications in separate policies simultaneously using the '''Parent Policy system. | |||
:This allows you to "copy" the configuration of ''some'' applications from another policy, but not others - this makes doing things such as having different [[Web Filter]] settings across policies, but keeping the configuration of all other applications identical across policies. There is not usually a need to modify settings for applications like [[Virus Blocker]] or [[Spam Blocker]] between different user groups, however if it is necessary it only takes a few clicks. | |||
Please note that we will be using the example of a school a lot in this section as it is quite apt in showing how Policy Manager can help you with different user classes. This can be applied to any organization; just look for groups you can fit users into - Administrative Assistants, Marketing, or HR, you're free to choose. It can also apply to different sets of servers ( | Please note that we will be using the example of a school a lot in this section as it is quite apt in showing how Policy Manager can help you with different user classes. This can be applied to any organization; just look for groups you can fit users into - Administrative Assistants, Marketing, or HR, you're free to choose. It can also apply to different sets of servers (''i.e.'', a ''DMZ policy'' for handling public servers, and an ''Internal policy'' for handling internal user machines and a ''Wireless policy'' for handling wireless users) and it can also apply to different times of day (''i.e.'', a ''Lunchtime and After Hours policy'' and a ''Work Hours policy''). For simplicity the examples below will mostly use the school groups as an example. | ||
| Line 45: | Line 47: | ||
=== Getting Started with Policy Manager === | === Getting Started with Policy Manager === | ||
Policies provide a way to handle different settings for different sessions. Using our example, an NG Firewall protecting a school might have three different policies - Students, Teachers, and Administrators. These policies provide completely separate configurations for traffic processing, for example you could allow teachers to access Facebook but not students. | |||
NG Firewall will always have at least one policy, the '''Default Policy'''. You can rename but you cannot remove this policy. As mentioned before, you create [[Rules]] to send traffic to '''policies''' where it is processed by the '''applications'''. Policies are created from within Policy Manager, however you will use NG Firewall's web GUI itself to switch to and configure each policy. At the top of the web GUI, you will see '''Default Policy''' with an arrow next to it - clicking this arrow allows you to change the policy you're looking at, as well as access the [[Session Viewer]] and [[Host Viewer]] and open the Policy Manager Settings directly. | |||
==== Parent | ==== Parent Policies ==== | ||
When you first create a new | When you first create a new policy it will not contain any applications. You can add in any applications you want and configure them to your liking, or you can use the '''Parent Policy''' system. When creating a new policy using Policy Manager, you have the option to select a Parent Policy. If you use this option your new policy will be pre-populated with all applications and settings from the Parent Policy you selected, however it will look a ''bit'' different. | ||
When you view the new '''child''' | When you view the new '''child''' policy, the application faceplates will be greyed out and you will be unable to click Settings. This is because the settings for these applications are being ''inherited'' from the parent policy, which is useful because it saves you from having to reconfigure applications you want operating the same way in multiple policies, such as the virus scanners. To change the settings or view the [[User_Guide#Event_Logs | Event Logs]], you'll need to open the application on the parent policy and use the drop-down to select the policy to view traffic for. | ||
If you want to modify the settings of an application in a child | If you want to modify the settings of an application in a child policy, you'll need to install the application you want to modify in the child policy - I know, it's already there, but you can't click Settings to modify the configuration. On the '''Apps''' tab on the left side of the web GUI, just click '''Install''' again. After a few seconds the app will re-appear and you will be able to click settings. Once this has happened, the new child application ''overrides'' the application inherited from the parent. The settings of the parent policy for this application '''have no effect for the application you have added to the child policy'''. If you're following along, your child policy will contain all applications that your parent policy does, however only one will have the Settings button enabled. | ||
To recap using our school example, we would send students to the Default | To recap using our school example, we would send students to the Default Policy, then create a new Teacher Policy which uses the Default Policy as its Parent Policy. If you go to the Teacher Policy, all the apps will be greyed out and you will not be able to modify any settings because they are copied from the Default Policy. By adding in a new copy of Web Filter, you can modify the settings so the teachers can access websites the students cannot, however settings for all other applications will still be copied from the Default Policy. | ||
== Settings == | == Settings == | ||
| Line 78: | Line 79: | ||
=== Policies === | === Policies === | ||
From this tab you can create new | From this tab you can create new policies, however please note you'll first need to create and save a policy before you can create a rule to apply traffic to that policy. | ||
To create a new | To create a new policy, simply click Add in the '''Policies''' section. | ||
*'''Name''': The name of this | *'''Name''': The name of this policy as displayed in the web GUI. | ||
*'''Description''': A description for this | *'''Description''': A description for this policy. | ||
*'''Parent | *'''Parent Policy''': Which policy (if any) this one should use as a [[#Parent Policies | Parent Policy]]. | ||
{{ServiceAppScreenshot|policy-manager|policies}} | {{ServiceAppScreenshot|policy-manager|policies}} | ||
| Line 92: | Line 93: | ||
=== Rules === | === Rules === | ||
If you've been reading up until this point, you may have guessed that this new | If you've been reading up until this point, you may have guessed that this new policy will do nothing until you send traffic to it. To accomplish this, you'll need to create a rule - click Add in the '''Rules''' tab. | ||
When each new session is processed, the rules are evaluated in order. If all of a sessions attributes match all of the criteria of a rule it is considered a match. The | When each new session is processed, the rules are evaluated in order. If all of a sessions attributes match all of the criteria of a rule it is considered a match. The policy for the first matching rule will be used to process the session. If no rules match, the ''Default Policy'' will be used to process the session. | ||
These rules operate as described in the [[Rules]] documentation. | These rules operate as described in the [[Rules]] documentation. | ||
Like many areas of | Like many areas of NG Firewall, the rules work from the top down. Let's go back to our school example and say we have three policies: Default (for students), Teacher and Administrative Staff. To get traffic to these policies, we would need to create two policies: one for the Teacher policy and one for the Administrative Staff policy - any traffic that did not match those two policies would be sent to the Default Policy. You can also explicitly add a rule sending traffic to the Default Policy, although it's not required. | ||
If the policy rule for the Teacher | If the policy rule for the Teacher policy is incorrect, it may end up matching ''all'' network traffic and sending it to the Teacher policy. Because it matches, the rule under it (for the Administrative Policy) will never be evaluated. On the flip side, if a rule is too narrow, it may not match the traffic you're trying to match at all, dumping it on the Default Policy. Because of this, we recommend starting out policy rules as very general (''e.g.'', match a few IPs or an entire subnet) and then tightening them down from there - let's look at some common example policies: | ||
[[Image:policy_rules.png|center|frame|Quick look at the rules table]] | [[Image:policy_rules.png|center|frame|Quick look at the rules table]] | ||
So this is the 'Rules' tab of the Policy Manager settings. On this page you will be able to see all of the rules that will be evaluated when determining which | So this is the '''Rules''' tab of the Policy Manager settings. On this page you will be able to see all of the rules that will be evaluated when determining which policy to direct a specific user or IP address. Pay attention to the 'Target Policy' column. Any users defined in the corresponding rule will be directed to that policy. Click on the page icon under the 'edit' column to define the rule. | ||
[[Image:policy_rules2.png|center|frame|Click 'edit' and define the rule]] | [[Image:policy_rules2.png|center|frame|Click 'edit' and define the rule]] | ||
Once you've clicked the edit button, this is where you'll end up. This is where you will define which users will be assigned to which | Once you've clicked the edit button, this is where you'll end up. This is where you will define which users will be assigned to which policy. You can specify a user using any one or combination of the identifiers in the drop down box. Any users that match the specified identifiers will be directed to the policy specified in the 'Target Policy' field. | ||
{{ServiceAppScreenshot|policy-manager|rules}} | {{ServiceAppScreenshot|policy-manager|rules}} | ||
| Line 120: | Line 121: | ||
== Related Topics == | == Related Topics == | ||
* [[ | * [[NG Firewall Rule Syntax]] | ||
* [[Directory Connector]] | * [[Directory Connector]] | ||
Latest revision as of 18:25, 3 May 2022
 Policy Manager Policy Manager
|
|
About Policy Manager
Policy Manager is one of NG Firewall's most powerful features. It works by allowing you to create multiple policies, which are different sets of applications configured differently for different use cases. Often you will configure all of NG Firewall apps to service the whole network, however often it is necessary to handle traffic for some users or network devices differently. For example, you may want Web Filter to be different for students vs teacher and you may want no Web Filtering at all for your servers. You may wish to run Captive Portal but only on the WiFi network or for unidentified devices. You may wish block certain applications with Application Control, but only at certain times of days.
In these cases, Policy Manager can simplify configuration a great deal by allowing for multiple sets of applications to be configured differently. Policy Manager allows creation of new policies beyond the "Default Policy". To address the above examples, the administrator can create a "Student Policy", "Teacher Policy", "After hours Policy", and "Wireless Network Policy" etc. Each policy can run a different set of applications configured differently. The Policy Manager Rules can determine which policy handles which network sessions.
- Set up multiple policies for different users, hosts, networks, interfaces, times of day, days of week, etc.
- Choose what applications are running in each policies.
- Configure multiple applications in separate policies simultaneously using the Parent Policy system.
- This allows you to "copy" the configuration of some applications from another policy, but not others - this makes doing things such as having different Web Filter settings across policies, but keeping the configuration of all other applications identical across policies. There is not usually a need to modify settings for applications like Virus Blocker or Spam Blocker between different user groups, however if it is necessary it only takes a few clicks.
Please note that we will be using the example of a school a lot in this section as it is quite apt in showing how Policy Manager can help you with different user classes. This can be applied to any organization; just look for groups you can fit users into - Administrative Assistants, Marketing, or HR, you're free to choose. It can also apply to different sets of servers (i.e., a DMZ policy for handling public servers, and an Internal policy for handling internal user machines and a Wireless policy for handling wireless users) and it can also apply to different times of day (i.e., a Lunchtime and After Hours policy and a Work Hours policy). For simplicity the examples below will mostly use the school groups as an example.
Getting Started with Policy Manager
Policies provide a way to handle different settings for different sessions. Using our example, an NG Firewall protecting a school might have three different policies - Students, Teachers, and Administrators. These policies provide completely separate configurations for traffic processing, for example you could allow teachers to access Facebook but not students.
NG Firewall will always have at least one policy, the Default Policy. You can rename but you cannot remove this policy. As mentioned before, you create Rules to send traffic to policies where it is processed by the applications. Policies are created from within Policy Manager, however you will use NG Firewall's web GUI itself to switch to and configure each policy. At the top of the web GUI, you will see Default Policy with an arrow next to it - clicking this arrow allows you to change the policy you're looking at, as well as access the Session Viewer and Host Viewer and open the Policy Manager Settings directly.
Parent Policies
When you first create a new policy it will not contain any applications. You can add in any applications you want and configure them to your liking, or you can use the Parent Policy system. When creating a new policy using Policy Manager, you have the option to select a Parent Policy. If you use this option your new policy will be pre-populated with all applications and settings from the Parent Policy you selected, however it will look a bit different.
When you view the new child policy, the application faceplates will be greyed out and you will be unable to click Settings. This is because the settings for these applications are being inherited from the parent policy, which is useful because it saves you from having to reconfigure applications you want operating the same way in multiple policies, such as the virus scanners. To change the settings or view the Event Logs, you'll need to open the application on the parent policy and use the drop-down to select the policy to view traffic for.
If you want to modify the settings of an application in a child policy, you'll need to install the application you want to modify in the child policy - I know, it's already there, but you can't click Settings to modify the configuration. On the Apps tab on the left side of the web GUI, just click Install again. After a few seconds the app will re-appear and you will be able to click settings. Once this has happened, the new child application overrides the application inherited from the parent. The settings of the parent policy for this application have no effect for the application you have added to the child policy. If you're following along, your child policy will contain all applications that your parent policy does, however only one will have the Settings button enabled.
To recap using our school example, we would send students to the Default Policy, then create a new Teacher Policy which uses the Default Policy as its Parent Policy. If you go to the Teacher Policy, all the apps will be greyed out and you will not be able to modify any settings because they are copied from the Default Policy. By adding in a new copy of Web Filter, you can modify the settings so the teachers can access websites the students cannot, however settings for all other applications will still be copied from the Default Policy.
Settings
This section reviews the different settings and configuration options available for Policy Manager.
Status
This displays the current status and some statistics.
Policies
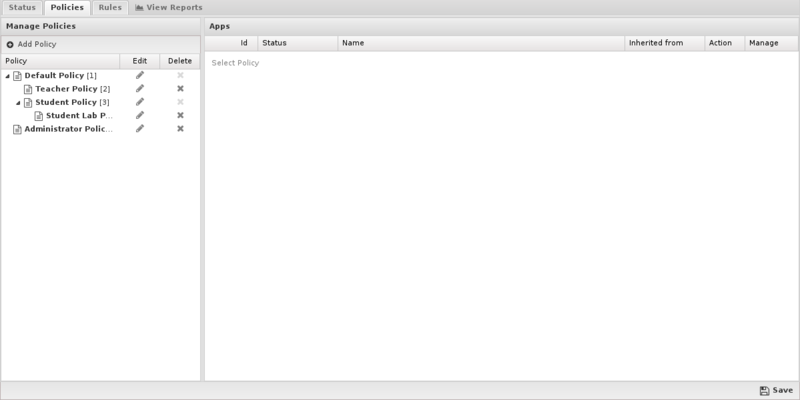
From this tab you can create new policies, however please note you'll first need to create and save a policy before you can create a rule to apply traffic to that policy.
To create a new policy, simply click Add in the Policies section.
- Name: The name of this policy as displayed in the web GUI.
- Description: A description for this policy.
- Parent Policy: Which policy (if any) this one should use as a Parent Policy.
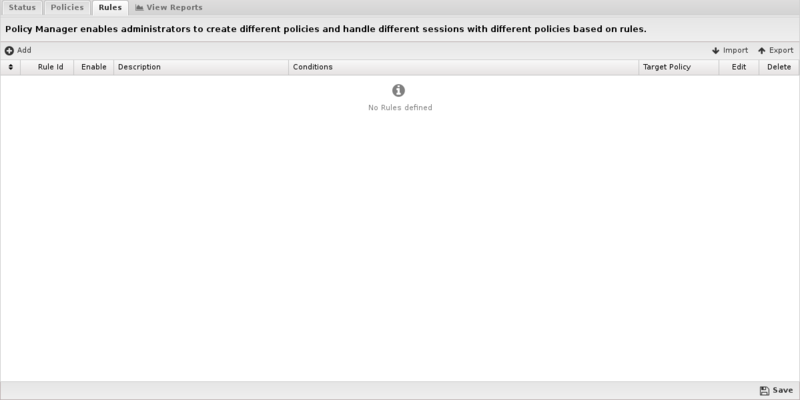
Rules
If you've been reading up until this point, you may have guessed that this new policy will do nothing until you send traffic to it. To accomplish this, you'll need to create a rule - click Add in the Rules tab.
When each new session is processed, the rules are evaluated in order. If all of a sessions attributes match all of the criteria of a rule it is considered a match. The policy for the first matching rule will be used to process the session. If no rules match, the Default Policy will be used to process the session.
These rules operate as described in the Rules documentation.
Like many areas of NG Firewall, the rules work from the top down. Let's go back to our school example and say we have three policies: Default (for students), Teacher and Administrative Staff. To get traffic to these policies, we would need to create two policies: one for the Teacher policy and one for the Administrative Staff policy - any traffic that did not match those two policies would be sent to the Default Policy. You can also explicitly add a rule sending traffic to the Default Policy, although it's not required.
If the policy rule for the Teacher policy is incorrect, it may end up matching all network traffic and sending it to the Teacher policy. Because it matches, the rule under it (for the Administrative Policy) will never be evaluated. On the flip side, if a rule is too narrow, it may not match the traffic you're trying to match at all, dumping it on the Default Policy. Because of this, we recommend starting out policy rules as very general (e.g., match a few IPs or an entire subnet) and then tightening them down from there - let's look at some common example policies:
So this is the Rules tab of the Policy Manager settings. On this page you will be able to see all of the rules that will be evaluated when determining which policy to direct a specific user or IP address. Pay attention to the 'Target Policy' column. Any users defined in the corresponding rule will be directed to that policy. Click on the page icon under the 'edit' column to define the rule.
Once you've clicked the edit button, this is where you'll end up. This is where you will define which users will be assigned to which policy. You can specify a user using any one or combination of the identifiers in the drop down box. Any users that match the specified identifiers will be directed to the policy specified in the 'Target Policy' field.
Reports
The Reports tab provides a view of all reports and events for all traffic handled by Policy Manager.
Reports
This applications reports can be accessed via the Reports tab at the top or the Reports tab within the settings. All pre-defined reports will be listed along with any custom reports that have been created.
Reports can be searched and further defined using the time selectors and the Conditions window at the bottom of the page. The data used in the report can be obtained on the Current Data window on the right.
Pre-defined report queries: {{#section:All_Reports|'Policy Manager'}}
The tables queried to render these reports:
Related Topics
Policy Manager FAQs
When should I create a new policy?
You should create a new policy when you want to apply different rules to different users. For more information, see Deciding When To Use Multiple Virtual Policies.
Can I use my existing Active Directory groups to create policies for different groups of users?
Yes, if you're using Directory Connector to authenticate against Active Directory you can create policies by username or group name. Simply set up the policy to your liking, click Users, and you will be able to select your users and groups from the list.
I'm using NG Firewall's OpenVPN application. Do I need to create policies for the VPN users? 💡
You do not have to create extra policies to use OpenVPN; by default its traffic will go through the Default Policy. You can use the Firewall app o allow or deny VPN users access to resources, or if you prefer you can create a new policy only for OpenVPN users. Furthermore, if you do not want OpenVPN traffic filtered at all, create a rule for all OpenVPN clients and select "No Policy" as the target policy.
I only want to scan inbound email traffic, not outbound. Do I need to create a new policy?
No - by default, outbound email traffic is not scanned. If you would like it to be, this option is available in Spam Blocker, however we highly recommend against it.