Certificates: Difference between revisions
No edit summary |
No edit summary |
||
| (10 intermediate revisions by 2 users not shown) | |||
| Line 7: | Line 7: | ||
==About Digital Certificates== | ==About Digital Certificates== | ||
NG Firewall uses | |||
[http://en.wikipedia.org/wiki/Digital_Certificate digital certificates] | [http://en.wikipedia.org/wiki/Digital_Certificate digital certificates] | ||
when serving web content via | when serving web content via | ||
[http:// | [http://eelln.wikipedia.org/wiki/Secure_Sockets_Layer SSL]. | ||
The server certificate is mainly used to provide secure access to the Administrative Console, as well as | The server certificate is mainly used to provide secure access to the Administrative Console, as well as | ||
the Email Quarantine features. The server also needs to generate imitation certificates on the fly when | the Email Quarantine features. The server also needs to generate imitation certificates on the fly when | ||
| Line 19: | Line 19: | ||
# Create a Certificate Signing Request [http://en.wikipedia.org/wiki/Certificate_signing_request (CSR)] which you can have signed by a third party certificate authority. | # Create a Certificate Signing Request [http://en.wikipedia.org/wiki/Certificate_signing_request (CSR)] which you can have signed by a third party certificate authority. | ||
If you plan on using the | If you plan on using the SSL Inspector application, option #1 is likely a good choice. Since you'll need to | ||
install the root certificate on all client computers and devices to use | install the root certificate on all client computers and devices to use SSL Inspector effectively, it makes | ||
sense to also sign the certificate used by the | sense to also sign the certificate used by the NG Firewall server with this same CA. | ||
If you aren't going to use the | If you aren't going to use the SSL Inspector, or have some other reason to prefer a third party | ||
certificate, then option #2 may be a better choice. This will allow you to obtain and use a server | certificate, then option #2 may be a better choice. This will allow you to obtain and use a server | ||
certificate signed by a third party authority. The benefit here, assuming you use one of the | certificate signed by a third party authority. The benefit here, assuming you use one of the | ||
| Line 34: | Line 34: | ||
[http://en.wikipedia.org/wiki/Certificate_Authority (CA)] | [http://en.wikipedia.org/wiki/Certificate_Authority (CA)] | ||
was created automatically. This CA is used to create and sign imitation certificates that are generated on | was created automatically. This CA is used to create and sign imitation certificates that are generated on | ||
the fly by the | the fly by the SSL Inspector application. It was also used to sign the default server certificate used | ||
by the server itself. You can use the default CA as is, or you can generate a new CA if you want to | by the server itself. You can use the default CA as is, or you can generate a new CA if you want to | ||
customize the information contained in the root certificate. | customize the information contained in the root certificate. | ||
| Line 47: | Line 47: | ||
===Download Root Certificate=== | ===Download Root Certificate=== | ||
Click this button to download the root_authority.crt certificate file of the Certificate Authority on | Click this button to download the root_authority.crt certificate file of the Certificate Authority on | ||
the | the NG Firewall server. If you are using SSL Inspector, or if you have configured your NG Firewall server | ||
to use a server certificate signed by the internal Certificate Authority, you will need to download | to use a server certificate signed by the internal Certificate Authority, you will need to download | ||
and install this certificate on all client computers and devices to eliminate certificate warning messages | and install this certificate on all client computers and devices to eliminate certificate warning messages | ||
when browsing or accessing secure content. | when browsing or accessing secure content. | ||
=== | Alternatively, you can download the certificate from a client system by navigating to http://yourserver/cert. | ||
This | |||
===Upload Root Certificate (CA)=== | |||
This option enables you to upload the root certificate and key files you may have generated using a different source. You can either paste the contents of the certificate and key files or upload the PEM formatted files. | |||
===View other Root Certificate Authorities=== | |||
This option enables you to view other Root Certificates that you may have previously uploaded. If necessary, you can revert back to a previous Root Certificate. | |||
==Server Certificate== | ==Server Certificate== | ||
The Server Certificate is used to secure all HTTPS connections with the | The Server Certificate is used to secure all HTTPS connections with the NG Firewall server. This mainly | ||
applies to the Administrative Console and the Email Quarantine pages. | applies to the Administrative Console and the Email Quarantine pages. | ||
| Line 73: | Line 78: | ||
Once the form is complete and you click the Generate button, the new server certificate will be | Once the form is complete and you click the Generate button, the new server certificate will be | ||
created and the | created and the NG Firewall server will start using it immediately. The Server Certificate information | ||
fields will also be updated to display the contents of the new certificate. | fields will also be updated to display the contents of the new certificate. | ||
==Third Party Certificate== | ==Third Party Certificate== | ||
Instead of using a certificate signed by the local CA, you may instead prefer to have the | Instead of using a certificate signed by the local CA, you may instead prefer to have the NG Firewall server | ||
use a certificate signed by well-known CA such as VeriSign or Thawte. The advantage to using this type | use a certificate signed by well-known CA such as VeriSign or Thawte. The advantage to using this type | ||
of certificate is client computers and devices will need no additional configuration, since most browsers | of certificate is client computers and devices will need no additional configuration, since most browsers | ||
are already configured to trust certificates issued by these authorities. | are already configured to trust certificates issued by these authorities. | ||
'''NOTE:''' This has nothing to do with [[SSL Inspector]] and is just the certificate used when connecting to web services running on the NG Firewall server itself (Administration, Captive Portal, Quarantine, and so on). | |||
===Upload Server Certificate=== | ===Upload Server Certificate=== | ||
| Line 88: | Line 95: | ||
Alternatively, instead of importing files you can copy & paste the certificate, key, and intermediate certificates provided by the CA into the fields. | Alternatively, instead of importing files you can copy & paste the certificate, key, and intermediate certificates provided by the CA into the fields. | ||
===Create Signature Signing Request=== | ===Create Signature Signing Request=== | ||
| Line 97: | Line 103: | ||
the "owner" of the website for which you are requesting the certificate. When they receive all the | the "owner" of the website for which you are requesting the certificate. When they receive all the | ||
required information, and any associated fee, they will issue you a new certificate file which you | required information, and any associated fee, they will issue you a new certificate file which you | ||
can upload to the | can upload to the NG Firewall server. | ||
===Import Signing Request Certificate=== | ===Import Signing Request Certificate=== | ||
When you receive your signed certificate, click the ''Import Signing | '''NOTE:''' Before importing your signed certificate, make sure it is formatted as a PEM file. This format is common with Apache or Linux type systems. If your certificate is not in PEM format, you need to re-download the certificate in PEM format from your certificate authority, or you can use tools such as OpenSSL to convert the certificate into the correct format. | ||
When you receive your signed certificate, click the ''Import Signing Request Certificate'' button to upload the certificate to the NG Firewall server. Certificates are provided in many different formats. | |||
You can select the ''Import a certificate file'' to upload a certificate file provided by the signer. This will parse the file and put the result in the displayed ''Server Certificate'' field and any other optional "Intermediate Certificates" in the ''Optional Intermediate Certificates'' field. To finish the upload click the ''Upload Certificate'' button. | You can select the ''Import a certificate file'' to upload a certificate file provided by the signer. This will parse the file and put the result in the displayed ''Server Certificate'' field and any other optional "Intermediate Certificates" in the ''Optional Intermediate Certificates'' field. To finish the upload click the ''Upload Certificate'' button. | ||
Alternatively, you can copy paste the certificate (text) provided by the signer into the fields and click ''Upload Certificate''. | Alternatively, you can copy paste the certificate (text) provided by the signer into the fields and click ''Upload Certificate''. | ||
Latest revision as of 16:13, 3 May 2022
Certificates
About Digital Certificates
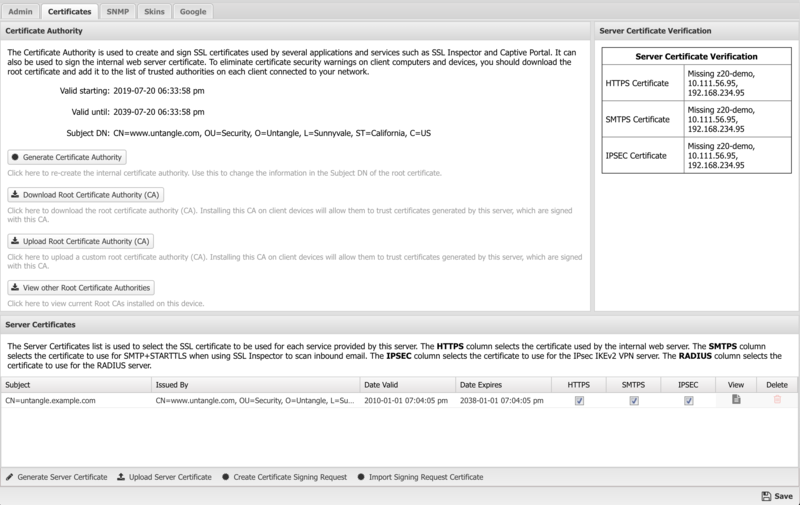
NG Firewall uses digital certificates when serving web content via SSL. The server certificate is mainly used to provide secure access to the Administrative Console, as well as the Email Quarantine features. The server also needs to generate imitation certificates on the fly when using the SSL Inspector application. There are two different ways to configure the certificate used by your server, depending on your specific requirements:
- Create and use a server certificate signed by the internal certificate authority
- Create a Certificate Signing Request (CSR) which you can have signed by a third party certificate authority.
If you plan on using the SSL Inspector application, option #1 is likely a good choice. Since you'll need to install the root certificate on all client computers and devices to use SSL Inspector effectively, it makes sense to also sign the certificate used by the NG Firewall server with this same CA.
If you aren't going to use the SSL Inspector, or have some other reason to prefer a third party certificate, then option #2 may be a better choice. This will allow you to obtain and use a server certificate signed by a third party authority. The benefit here, assuming you use one of the standard and well known providers, is that their root certificate will already be included in the list of trusted CA's on client computers and devices, so you won't have to distribute and install a new root certificate.
Certificate Authority
During the initial server installation, a default Certificate Authority (CA) was created automatically. This CA is used to create and sign imitation certificates that are generated on the fly by the SSL Inspector application. It was also used to sign the default server certificate used by the server itself. You can use the default CA as is, or you can generate a new CA if you want to customize the information contained in the root certificate.
Generate Certificate Authority
When you click this button to generate a new CA, you will be presented with a popup form where you can enter the details to be included in the Subject DN of the new root certificate. Since this operation is creating a root certificate and not a server certificate, the CN field can contain most anything you like. Once the form is complete and you click the Generate button, the new CA will be created and the Certificate Authority information fields will be updated to display the contents of the new certificate.
Download Root Certificate
Click this button to download the root_authority.crt certificate file of the Certificate Authority on the NG Firewall server. If you are using SSL Inspector, or if you have configured your NG Firewall server to use a server certificate signed by the internal Certificate Authority, you will need to download and install this certificate on all client computers and devices to eliminate certificate warning messages when browsing or accessing secure content.
Alternatively, you can download the certificate from a client system by navigating to http://yourserver/cert.
Upload Root Certificate (CA)
This option enables you to upload the root certificate and key files you may have generated using a different source. You can either paste the contents of the certificate and key files or upload the PEM formatted files.
View other Root Certificate Authorities
This option enables you to view other Root Certificates that you may have previously uploaded. If necessary, you can revert back to a previous Root Certificate.
Server Certificate
The Server Certificate is used to secure all HTTPS connections with the NG Firewall server. This mainly applies to the Administrative Console and the Email Quarantine pages.
During the initial server installation, a default certificate is created and signed using the default Certificate Authority that was also created during installation. You can use the default root certificate as is, or you can generate a new server certificate if you want to customize the information contained in the server certificate.
Generate Server Certificate
When you click this button to generate a new server certificate, you will be presented with a popup form where you can enter the details to be included in the Subject DN of the server certificate. All fields are optional except for the Common Name (CN) field, which should contain the hostname that will be used to access the server.
Example: hostname.domain.com
Once the form is complete and you click the Generate button, the new server certificate will be created and the NG Firewall server will start using it immediately. The Server Certificate information fields will also be updated to display the contents of the new certificate.
Third Party Certificate
Instead of using a certificate signed by the local CA, you may instead prefer to have the NG Firewall server use a certificate signed by well-known CA such as VeriSign or Thawte. The advantage to using this type of certificate is client computers and devices will need no additional configuration, since most browsers are already configured to trust certificates issued by these authorities.
NOTE: This has nothing to do with SSL Inspector and is just the certificate used when connecting to web services running on the NG Firewall server itself (Administration, Captive Portal, Quarantine, and so on).
Upload Server Certificate
Click the Upload Server Certificate button to upload an official signed certificate provided by a CA, or a certificate that you generated yourself.
Certificates from CAs are provided in many different formats. The Import a certificate or key file button can be used to upload the certificates and keys. First, press Import a certificate or key file and select the certificate. Second, press the Import a certificate or key file and select the private key file. Repeat this process for any additional separate intermediate certificates (not commonly required). When finished, the "Server Certificate" field should contain the server cert, and the "Certificate Key" field should contain the private key. Additionally the "Optional Intermediate Certificates" field may be populated if the CA provided an intermediate certificate. At this point click Upload Certificate to upload the certificate. Don't forget to adjust how the new certificate will be used (HTTPS, IPSEC, etc) in the Server Certificates table!
Alternatively, instead of importing files you can copy & paste the certificate, key, and intermediate certificates provided by the CA into the fields.
Create Signature Signing Request
Click the Create Signature Signing Request button to generate a signature signing request, you will be presented with a popup form where you can enter the details to be included in the Subject DN of the CSR. Once the form is complete and you click Generate, a server_certificate.csr file will be downloaded to your computer. The certificate authority you choose will require this file, and possibly additional information to verify that you are the "owner" of the website for which you are requesting the certificate. When they receive all the required information, and any associated fee, they will issue you a new certificate file which you can upload to the NG Firewall server.
Import Signing Request Certificate
NOTE: Before importing your signed certificate, make sure it is formatted as a PEM file. This format is common with Apache or Linux type systems. If your certificate is not in PEM format, you need to re-download the certificate in PEM format from your certificate authority, or you can use tools such as OpenSSL to convert the certificate into the correct format.
When you receive your signed certificate, click the Import Signing Request Certificate button to upload the certificate to the NG Firewall server. Certificates are provided in many different formats.
You can select the Import a certificate file to upload a certificate file provided by the signer. This will parse the file and put the result in the displayed Server Certificate field and any other optional "Intermediate Certificates" in the Optional Intermediate Certificates field. To finish the upload click the Upload Certificate button.
Alternatively, you can copy paste the certificate (text) provided by the signer into the fields and click Upload Certificate.