Threat Prevention: Difference between revisions
Bcarmichael (talk | contribs) No edit summary |
|||
| (54 intermediate revisions by 5 users not shown) | |||
| Line 1: | Line 1: | ||
[[Category:Applications]] | [[Category:Applications]] | ||
<span style="display:none" class="helpSource | <span style="display:none" class="helpSource threat_prevention">Threat_Prevention</span> | ||
<span style="display:none" class="helpSource | <span style="display:none" class="helpSource threat_prevention_status">Threat_Prevention#Status</span> | ||
<span style="display:none" class="helpSource | <span style="display:none" class="helpSource threat_prevention_threats">Threat_Prevention#Threats</span> | ||
<span style="display:none" class="helpSource | <span style="display:none" class="helpSource threat_prevention_rules">Threat_Prevention#Rules</span> | ||
<span style="display:none" class="helpSource threat_prevention_lookup">Threat_Prevention#Threat_Lookup</span> | |||
{| width='100%' | {| width='100%' | ||
|- | |- | ||
| align="center" | [[Image:ThreatPrevention.png| | | align="center" | [[Image:ThreatPrevention.png|128px]] '''Threat Prevention''' | ||
| align="center" | | | align="center" | | ||
{| | {| | ||
| Line 13: | Line 14: | ||
| Other Links: | | Other Links: | ||
|- | |- | ||
|[http:// | |[http://forums.untangle.com/threat-prevention/ Threat Prevention Forums] | ||
|- | |- | ||
|[[Threat Prevention Reports]] | |[[Threat Prevention Reports]] | ||
| Line 28: | Line 25: | ||
== About | == About Threat Prevention == | ||
Threat Prevention blocks potentially harmful traffic from entering or exiting the network. This app can prevent cyber attacks to your servers (e.g. web, VoIP, and email). It is also useful to prevent data loss in case users mistakenly try to connect to a phishing site or other type of malicious host. | |||
The | Threat Prevention uses Threat Intelligence technology managed by Webroot BrightCloud®. Webroot BrightCloud® assesses each IP address and provides it a reputation score. The reputation score is the result of running an IP address through BrightCloud’s sensor network. The Sensor Network analyzes the IP address based on real time Global Threat Databases that are kept up to date with new and emerging threats. The Threat Prevention app works by performing a query to the BrightCloud® service, requesting for the reputation score and historical data of each IP address or URL. Based on the rating of the IP address or URL, the session may be blocked. By default, the Threat Prevention app blocks sessions with a "High Risk" rating. IP addresses or URLs rated as High Risk may be associated with the following types of attacks: | ||
* Spam Sources - IP addresses involved in tunneling spam messages through proxy, anomalous SMTP activities, and forum spam activities. | |||
* Windows Exploits - IP addresses participating in the distribution of malware, shell code, rootkits, worms or viruses for Windows platforms. | |||
* Web Attacks - IP addresses using cross site scripting, iFrame injection, SQL injection, cross domain injection, or domain password brute force attacks to target vulnerabilities on a web server. | |||
* Botnets - IP addresses acting as Botnet Command and Control (C&C) centers, and infected zombie machines controlled by the C&C servers. | |||
* Denial of Service
- The Denial of Service category includes DOS, DDOS, anomalous sync flood, and anomalous traffic detection. | |||
* Scanners - IP addresses involved in unauthorized reconnaissance activities such as probing, host scanning, port scanning and brute force login attempts. | |||
* Phishing - IP addresses hosting phishing sites and sites related to other kinds of fraudulent activities. | |||
* TOR Proxy - IP addresses acting as exit nodes for the TOR Network. Exit nodes are the last point along the proxy chain and make a direct connection to the originator’s intended destination. | |||
* Proxy - IP addresses providing proxy services, including both
VPN and open web proxy services. | |||
* Mobile Threats - Denial of service, packet sniffing, address impersonation,
and session hijacking | |||
== Settings == | |||
This section reviews the different settings and configuration options available for Threat Prevention. | |||
== | === Status === | ||
The Status screen shows the running state of Threat Prevention and relevant Metrics such as the number of blocked sessions and high risk threats. | |||
[[File:Apps threat-prevention status.png|800px|thumb|center]] | |||
<div align="center">[[File:Play-circle.png|link=http://demo.untangle.com/admin/index.do#apps/1/threat-prevention/status]] | |||
[http://demo.untangle.com/admin/index.do#apps/1/threat-prevention/status view on demo]</div> | |||
=== Threats === | |||
In the Threats tab you can review the threshold for IP Addresses and URL Threats. The recommended and default Reputation Threshold is "High Risk". "High Risk" is the only setting that should be deployed without reviewing and understanding the implications on network traffic. 'Suspicious" will block significantly more network traffic than "High Risk" will block. | |||
== | [[File:Apps threat-prevention threats.png|800px|thumb|center]] | ||
<div align="center">[[File:Play-circle.png|link=http://demo.untangle.com/admin/index.do#apps/1/threat-prevention/threats]] | |||
[http://demo.untangle.com/admin/index.do#apps/1/threat-prevention/threats view on demo]</div> | |||
=== Pass Sites === | |||
The '''Pass Sites''' tab allows you to specify IP Addresses or URLs to exclude from Threat Prevention lookups to ensure they are permitted by this app. | |||
[[File:Apps threat-prevention pass-sites.png|800px|thumb|center]] | |||
<div align="center">[[File:Play-circle.png|link=http://demo.untangle.com/admin/index.do#apps/1/threat-prevention/pass-sites]] | |||
[http://demo.untangle.com/admin/index.do#apps/1/threat-prevention/pass-sites view on demo]</div> | |||
=== Rules === | === Rules === | ||
The '''Rules''' tab allows you to specify rules to Block, Pass or Flag traffic that crosses the | The '''Rules''' tab allows you to specify rules to Block, Pass or Flag traffic that crosses the NG Firewall. | ||
The [[Rules|Rules documentation]] describes how rules work and how they are configured. Threat Prevention uses rules to determine to block/pass the specific session, and if the sessions is flagged. Flagging a session marks it in the logs for reviewing in the event logs or reports, but has no direct effect on the network traffic. | |||
In addition to all the common rule types, there are four that are unique to Threat Prevention, and these can be useful for making exceptions to the general *Reputation Threshold* setting. | |||
The | '''Client address reputation''' | ||
The reputation value of a source IP address returned by the Webroot BrightCloud® service. This applies to incoming connections from the Internet to open services on your network. | |||
'''Server address reputation''' | |||
The reputation value of a destination IP address returned by the Webroot BrightCloud® service. This applies to outgoing connections to the Internet from hosts on your network. | |||
'''Client address category''' | |||
The reputation category of a source IP address returned by the Webroot BrightCloud® service. This applies to incoming connections from the Internet to open services on your network. | |||
=== Rule Actions === | '''Server address category''' | ||
The reputation category of a destination IP address returned by the Webroot BrightCloud® service. This applies to outgoing connections to the Internet from hosts on your network. | |||
==== Rule Actions ==== | |||
* '''Pass''': Allows the traffic which matched the rule to flow. | * '''Pass''': Allows the traffic which matched the rule to flow. | ||
| Line 67: | Line 96: | ||
Additionally a session can be flagged. If '''Flag''' is checked the event is flagged for easier viewing in the event log. Flag is always enabled if the action is Block. | Additionally a session can be flagged. If '''Flag''' is checked the event is flagged for easier viewing in the event log. Flag is always enabled if the action is Block. | ||
[[File:Apps threat-prevention rules.png|800px|thumb|center]] | |||
<div align="center">[[File:Play-circle.png|link=http://demo.untangle.com/admin/index.do#apps/1/threat-prevention/rules]] | |||
[http://demo.untangle.com/admin/index.do#apps/1/threat-prevention/rules view on demo]</div> | |||
=== Threat Lookup === | |||
Threat Lookup enables you to get threat information on an IP Address or URL. This is useful to validate afterwards or confirm in advance the Reputation and other details of the IP Address or URL. | |||
Enter an IP Address or URL in the input field and click '''Search''' to get information. | |||
== | [[File:Apps threat-prevention threat-lookup.png|800px|thumb|center]] | ||
<div align="center">[[File:Play-circle.png|link=http://demo.untangle.com/admin/index.do#apps/1/threat-prevention/lookup]] | |||
[http://demo.untangle.com/admin/index.do#apps/1/threat-prevention/lookup view on demo]</div> | |||
==== Threat Results ==== | |||
{| border="1" cellpadding="2" width="85%%" align="center" | |||
!Result | |||
!Description | |||
|- | |||
| width="25%" | Address/URL | |||
| width="60%" | The IP Address or URL you requested to search. | |||
|- | |||
| width="25%" | Country | |||
| width="60%" | The country where the IP Address or URL originates. | |||
|- | |||
| width="25%" | Popularity | |||
| width="60%" | The popularity of the IP Address or URL based on the volume of lookups. | |||
|- | |||
| width="25%" | Recent Threat Count | |||
| width="60%" | The amount of recent occurrences that the IP Address or URL has been associated to a threat. | |||
|- | |||
| width="25%" | Age | |||
| width="60%" | The amount of time since the IP Address or URL was first noticed. | |||
|- | |||
| width="25%" | Reputation | |||
| width="60%" | The reputation of the IP Address or URL as determined by the Webroot BrightCloud reputation service. | |||
|- | |||
| width="25%" | Details | |||
| width="60%" | A description of the Reputation value. | |||
|- | |||
|} | |||
=== Advanced === | |||
The Advanced section enables you to configure additional Threat Prevention options. | |||
'''Custom block page URL:''' Set an external location where to redirect users when they are denied access to a web site by Threat Prevention. This is useful if you want to use your own server to process the denial in a different way than the built-in denial options. | |||
Enabling this option will only redirect internal/outbound traffic to your custom page. It will not function to redirect external/inbound traffic (such as Port Forwarded traffic). | |||
'''Block Options:''' | |||
''Close connection for blocked HTTPS sessions without redirecting to block page'' If enabled, secure sites blocked by Threat Prevention do not redirect the user to a denial page and close the connection without any notice to the user. This is useful when you are not using [[SSL Inspector]] and the server's root certificate is not installed on the client device. | |||
[[File:Apps threat-prevention advanced.png|800px|thumb|center]] | |||
<div align="center">[[File:Play-circle.png|link=http://demo.untangle.com/admin/index.do#apps/1/threat-prevention/advanced]] | |||
[http://demo.untangle.com/admin/index.do#apps/1/threat-prevention/advanced view on demo]</div> | |||
== | == Reports == | ||
{{:Threat Prevention Reports}} | |||
== Threat Prevention FAQs == | |||
== | === Why is the client reputation score different from the [https://www.brightcloud.com/tools/url-ip-lookup.php BrightCloud Online Lookup tool?] === | ||
The Webroot BrightCloud lookup tool shows the server reputation score only. When using the Threat Prevention lookup tool within NG Firewall, the result shows both the client and server reputation scores. The reputation applied to the session depends on the direction. For incoming sessions the client reputation is used. For outgoing sessions the server reputation is used. | |||
Latest revision as of 18:47, 4 April 2023
 Threat Prevention Threat Prevention
|
|
About Threat Prevention
Threat Prevention blocks potentially harmful traffic from entering or exiting the network. This app can prevent cyber attacks to your servers (e.g. web, VoIP, and email). It is also useful to prevent data loss in case users mistakenly try to connect to a phishing site or other type of malicious host.
Threat Prevention uses Threat Intelligence technology managed by Webroot BrightCloud®. Webroot BrightCloud® assesses each IP address and provides it a reputation score. The reputation score is the result of running an IP address through BrightCloud’s sensor network. The Sensor Network analyzes the IP address based on real time Global Threat Databases that are kept up to date with new and emerging threats. The Threat Prevention app works by performing a query to the BrightCloud® service, requesting for the reputation score and historical data of each IP address or URL. Based on the rating of the IP address or URL, the session may be blocked. By default, the Threat Prevention app blocks sessions with a "High Risk" rating. IP addresses or URLs rated as High Risk may be associated with the following types of attacks:
- Spam Sources - IP addresses involved in tunneling spam messages through proxy, anomalous SMTP activities, and forum spam activities.
- Windows Exploits - IP addresses participating in the distribution of malware, shell code, rootkits, worms or viruses for Windows platforms.
- Web Attacks - IP addresses using cross site scripting, iFrame injection, SQL injection, cross domain injection, or domain password brute force attacks to target vulnerabilities on a web server.
- Botnets - IP addresses acting as Botnet Command and Control (C&C) centers, and infected zombie machines controlled by the C&C servers.
- Denial of Service - The Denial of Service category includes DOS, DDOS, anomalous sync flood, and anomalous traffic detection.
- Scanners - IP addresses involved in unauthorized reconnaissance activities such as probing, host scanning, port scanning and brute force login attempts.
- Phishing - IP addresses hosting phishing sites and sites related to other kinds of fraudulent activities.
- TOR Proxy - IP addresses acting as exit nodes for the TOR Network. Exit nodes are the last point along the proxy chain and make a direct connection to the originator’s intended destination.
- Proxy - IP addresses providing proxy services, including both VPN and open web proxy services.
- Mobile Threats - Denial of service, packet sniffing, address impersonation, and session hijacking
Settings
This section reviews the different settings and configuration options available for Threat Prevention.
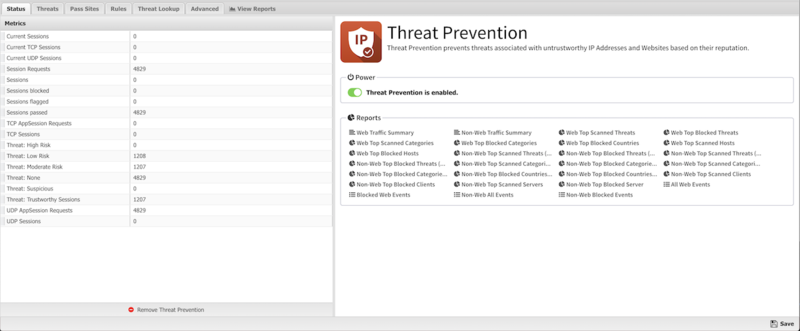
Status
The Status screen shows the running state of Threat Prevention and relevant Metrics such as the number of blocked sessions and high risk threats.
Threats
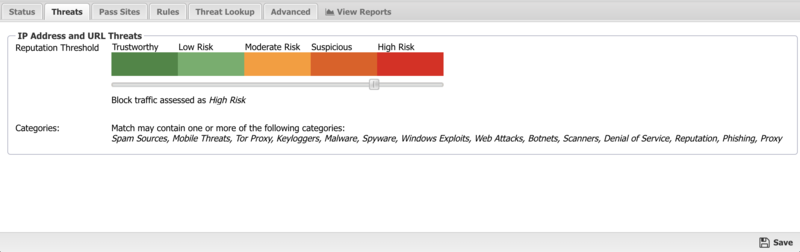
In the Threats tab you can review the threshold for IP Addresses and URL Threats. The recommended and default Reputation Threshold is "High Risk". "High Risk" is the only setting that should be deployed without reviewing and understanding the implications on network traffic. 'Suspicious" will block significantly more network traffic than "High Risk" will block.
Pass Sites
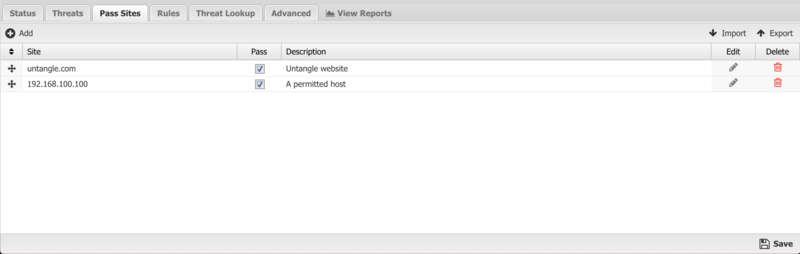
The Pass Sites tab allows you to specify IP Addresses or URLs to exclude from Threat Prevention lookups to ensure they are permitted by this app.
Rules
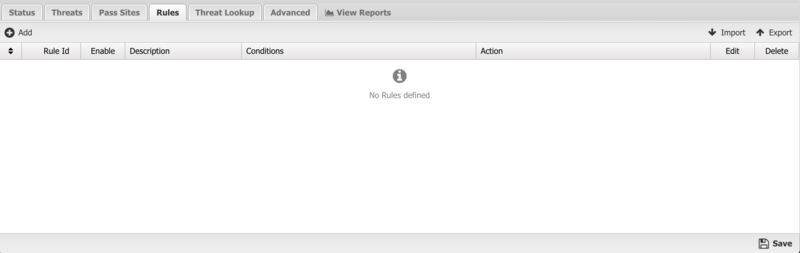
The Rules tab allows you to specify rules to Block, Pass or Flag traffic that crosses the NG Firewall.
The Rules documentation describes how rules work and how they are configured. Threat Prevention uses rules to determine to block/pass the specific session, and if the sessions is flagged. Flagging a session marks it in the logs for reviewing in the event logs or reports, but has no direct effect on the network traffic.
In addition to all the common rule types, there are four that are unique to Threat Prevention, and these can be useful for making exceptions to the general *Reputation Threshold* setting.
Client address reputation The reputation value of a source IP address returned by the Webroot BrightCloud® service. This applies to incoming connections from the Internet to open services on your network.
Server address reputation The reputation value of a destination IP address returned by the Webroot BrightCloud® service. This applies to outgoing connections to the Internet from hosts on your network.
Client address category The reputation category of a source IP address returned by the Webroot BrightCloud® service. This applies to incoming connections from the Internet to open services on your network.
Server address category The reputation category of a destination IP address returned by the Webroot BrightCloud® service. This applies to outgoing connections to the Internet from hosts on your network.
Rule Actions
- Pass: Allows the traffic which matched the rule to flow.
- Block: Blocks the traffic which matched the rule.
Additionally a session can be flagged. If Flag is checked the event is flagged for easier viewing in the event log. Flag is always enabled if the action is Block.
Threat Lookup
Threat Lookup enables you to get threat information on an IP Address or URL. This is useful to validate afterwards or confirm in advance the Reputation and other details of the IP Address or URL. Enter an IP Address or URL in the input field and click Search to get information.
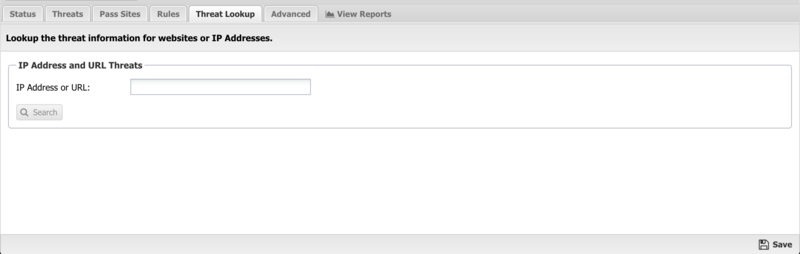
Threat Results
| Result | Description |
|---|---|
| Address/URL | The IP Address or URL you requested to search. |
| Country | The country where the IP Address or URL originates. |
| Popularity | The popularity of the IP Address or URL based on the volume of lookups. |
| Recent Threat Count | The amount of recent occurrences that the IP Address or URL has been associated to a threat. |
| Age | The amount of time since the IP Address or URL was first noticed. |
| Reputation | The reputation of the IP Address or URL as determined by the Webroot BrightCloud reputation service. |
| Details | A description of the Reputation value. |
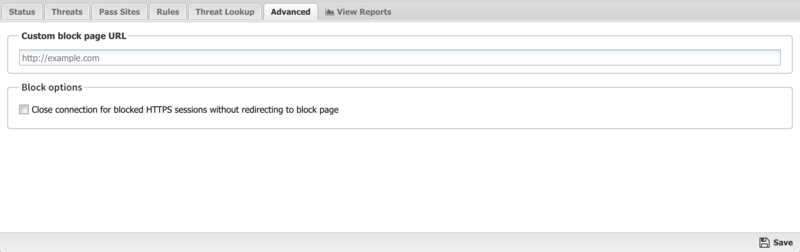
Advanced
The Advanced section enables you to configure additional Threat Prevention options.
Custom block page URL: Set an external location where to redirect users when they are denied access to a web site by Threat Prevention. This is useful if you want to use your own server to process the denial in a different way than the built-in denial options.
Enabling this option will only redirect internal/outbound traffic to your custom page. It will not function to redirect external/inbound traffic (such as Port Forwarded traffic).
Block Options: Close connection for blocked HTTPS sessions without redirecting to block page If enabled, secure sites blocked by Threat Prevention do not redirect the user to a denial page and close the connection without any notice to the user. This is useful when you are not using SSL Inspector and the server's root certificate is not installed on the client device.
Reports
Reports
This applications reports can be accessed via the Reports tab at the top or the Reports tab within the settings. All pre-defined reports will be listed along with any custom reports that have been created.
Reports can be searched and further defined using the time selectors and the Conditions window at the bottom of the page. The data used in the report can be obtained on the Current Data window on the right.
Pre-defined report queries: {{#section:All_Reports|'Threat Prevention'}}
The tables queried to render these reports:
Threat Prevention FAQs
Why is the client reputation score different from the BrightCloud Online Lookup tool?
The Webroot BrightCloud lookup tool shows the server reputation score only. When using the Threat Prevention lookup tool within NG Firewall, the result shows both the client and server reputation scores. The reputation applied to the session depends on the direction. For incoming sessions the client reputation is used. For outgoing sessions the server reputation is used.