RADIUS Proxy: Difference between revisions
(Created page with "<span style="display:none" class="helpSource local_directory_radius_proxy">RADIUS_Proxy</span> = Radius Proxy = ''Radius Proxy'' can be enabled to allow 802.1x wireless acce...") |
No edit summary |
||
| (7 intermediate revisions by 2 users not shown) | |||
| Line 1: | Line 1: | ||
<span style="display:none" class="helpSource local_directory_radius_proxy">RADIUS_Proxy</span> | <span style="display:none" class="helpSource local_directory_radius_proxy">RADIUS_Proxy</span> | ||
''Radius Proxy'' is an optional configuration of the [[RADIUS Server]] that enables [https://en.wikipedia.org/wiki/IEEE_802.1X 802.1X] authentication against an Active Directory server. Access points configured with WPA/WPA2 Enterprise authentication to the NG Firewall [[RADIUS Server]] can enforce login via Active Directory when joining the wireless network. | |||
== Prerequisites == | |||
The NG Firewall appliance must be able to resolve the fully qualified hostname of your Active Directory Primary Domain Controller. You can test name resolution using the DNS Test of the [[Troubleshooting]] utility. If the test fails, you must create a Static DNS Entry in the NG Firewall [[DNS Server]]. | |||
== Active Directory Server == | |||
There are three steps required to configure and verify your configuration with the RADIUS Proxy. | |||
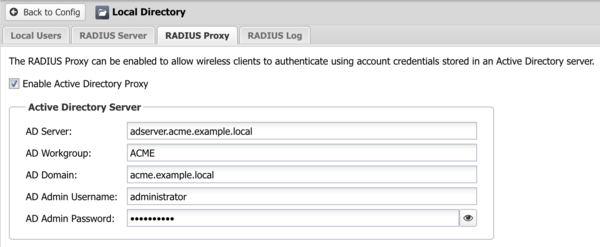
1. Input the Active Directory Server details and click Save to apply and activate the settings. | |||
'''Important''': The '''AD Workgroup''' should be in upper case. | |||
[[Image:Radius-proxy-config.png|600px|center|RADIUS Proxy Configuration]] | |||
2. Click the ''Create AD Computer Account'' button to register the NG Firewall server with the Active Directory server. If the operation is successful you should see the distinguishedName, whenCreated, and whenChanged fields in the ''AD Account Status'' field. | |||
[[Image:Radius_proxy_status.png|500px|center|RADIUS Proxy Status]] | |||
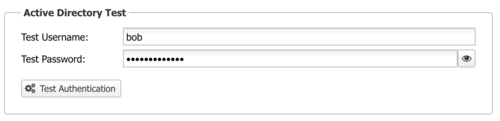
3 Enter a valid username and password in the ''Active Directory Test'' area and click ''Test Authentication''. You should see a message indicating the test was successful. | |||
[[Image:Radius_proxy_test.png|500px|center|RADIUS Proxy Test]] | |||
Latest revision as of 16:15, 3 May 2022
Radius Proxy is an optional configuration of the RADIUS Server that enables 802.1X authentication against an Active Directory server. Access points configured with WPA/WPA2 Enterprise authentication to the NG Firewall RADIUS Server can enforce login via Active Directory when joining the wireless network.
Prerequisites
The NG Firewall appliance must be able to resolve the fully qualified hostname of your Active Directory Primary Domain Controller. You can test name resolution using the DNS Test of the Troubleshooting utility. If the test fails, you must create a Static DNS Entry in the NG Firewall DNS Server.
Active Directory Server
There are three steps required to configure and verify your configuration with the RADIUS Proxy.
1. Input the Active Directory Server details and click Save to apply and activate the settings.
Important: The AD Workgroup should be in upper case.
2. Click the Create AD Computer Account button to register the NG Firewall server with the Active Directory server. If the operation is successful you should see the distinguishedName, whenCreated, and whenChanged fields in the AD Account Status field.
3 Enter a valid username and password in the Active Directory Test area and click Test Authentication. You should see a message indicating the test was successful.